ASICs (chips) that are counterfeit pose a serious threat to the electronics sector and may result in large financial losses. Chips that are counterfeit are getting more and more prevalent in developing countries where consumer demand is growing. We will discuss the issues with employing fake ASICs in this piece, as well as their dangers and cons and what we can do to prevent them. In addition, various tactics companies can use to prevent counterfeits and protect their intellectual property are discussed.

Fake Chips
Fake chips, also known as counterfeit chips, are chips that have been intentionally designed to appear as if they are genuine but are fake or fraudulent. These chips can be used for various purposes, such as to create fake products that mimic the performance of genuine products or to gain unauthorized access to sensitive information.
The increasing use of technologies and electronic devices such as mobile phones, PCs, and cars has led to a corresponding increase in demand for hardware. Unfortunately, this has also led to an increase in fake ASICs (chips) circulating in the market.
Typically, fake chips are made by replicating the shape and structure of the actual chip using less expensive components and methods. As a result, chips that appear to work well may not have the same performance, reliability, or security features as the original chip. As a result, counterfeit ASICs are often of lower quality than the real thing and may not perform as promised. It is crucial to purchase from an established dealer to prevent being duped by a fake ASIC. You can choose a reliable seller by reading reviews and conducting research. Moreover, confirm the legitimacy of the product you are purchasing by visiting the manufacturer’s website and checking for security features like tamper-proof packaging.
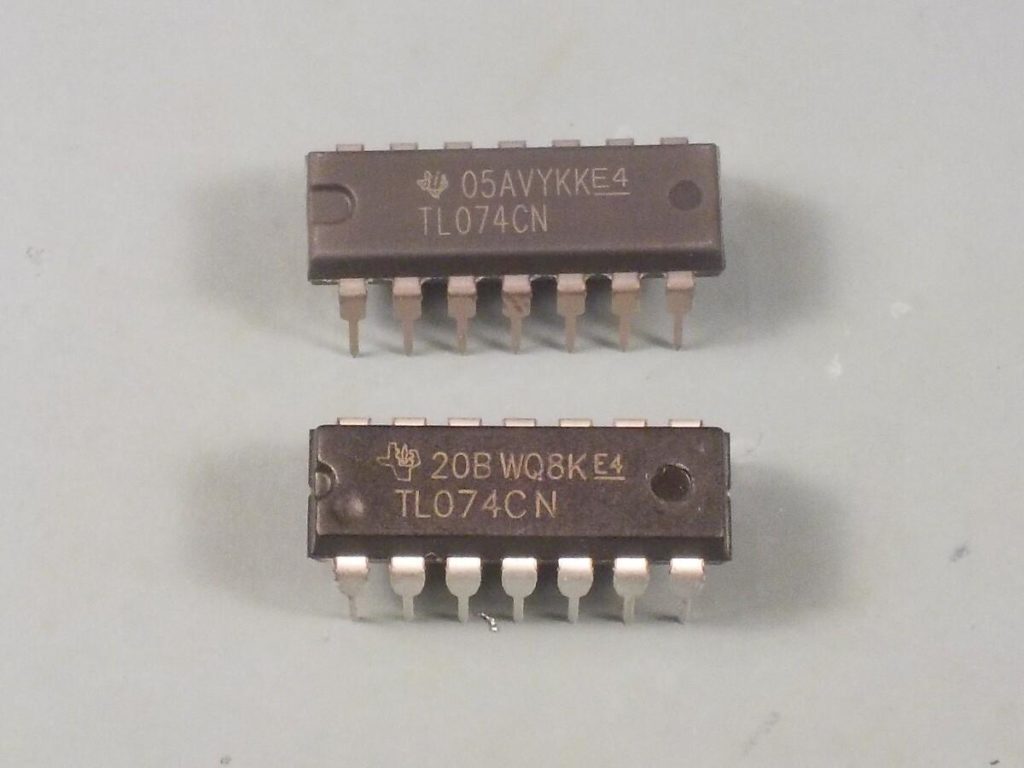
Figure 1: the difference between the fake and real chip in fonts and logos shape

Figure 2: the difference between the fake and real chip in fonts and shapes
Types of Counterfeit Chips
There are many types of fake ASICs (chips) on the market. Some of them are easy to spot, while others are more difficult as they have different characteristics and potential impacts. Here are some common types of fake ASICs:
- Re-marked chips: Re-marked chips are genuine chips with their markings altered to appear as a different chip, which can be done to make lower-performing chips appear to be higher-performing or to use up excess inventory. Re-marked chips can lead to reduced performance and reliability.
- Cloned chips: Cloned chips are chips copied from a genuine design and produced using cheaper materials and processes. These chips can have similar performance characteristics to genuine chips but may not have the same reliability or security features.
- Blacktop chips: Blacktop chips have had their surface ground off and replaced with a new surface that appears to be a different chip. This can be used to hide re-marking or cloning and can be difficult to detect without advanced testing.
- Recycled chips: Recycled chips have been salvaged from old or discarded electronic devices and then re-marked or cloned. These chips may be unreliable due to the wear and tear of their previous use.
- Counterfeit chips: Counterfeit chips have been produced to appear genuine but are actually fake or fraudulent. These chips can be produced using any of the methods above and can result in reduced performance, reliability, and security.
These fake chips can cause serious problems, including reduced performance, reliability, and security risks. It is important to take steps to prevent buying counterfeit chips and to work with reputable suppliers to ensure you purchase genuine, high-quality chips.
How to Protect a Chip from Counterfeiting?
Designing a chip to be challenging to replicate is the greatest approach to prevent it from being copied. This can be done using complex shapes, different materials, and complex patterns. Using encryption and security features that make it challenging to produce a false version of the chip is another approach to safeguard it. Various methods can be applied to lessen the chance of counterfeiting:
- Using security features: Security elements, such as holographic stickers, tamper-evident packaging, or anti-counterfeiting labels, can be incorporated into the chip design to prevent counterfeiting.
- Use unique identification: Using unique identification such as serial numbers, barcodes, or RFID tags can help identify genuine chips and prevent counterfeiting.
- Control the supply chain: Managing the supply chain from the producer to the final consumer can assist in stopping the entry of fake chips into the system. This can be done by using trusted suppliers and distributors and implementing strict quality control measures.
- Employ encryption and authentication: Implementing encryption and authentication features into the chip can help prevent unauthorized access and modification of the chip’s firmware.
- Monitor the market: Keeping an eye out for fake chips can help catch counterfeiters and stop the sale of fake goods.
- Use advanced verification techniques: Advanced verification techniques such as X-ray analysis or electrical testing can be used to verify the authenticity of chips. These techniques can be expensive and time-consuming, but they can provide a higher level of confidence that the chip is genuine.
What Problems Counterfeited Chips Cause?
Counterfeiting ASICs has become a serious problem in the electronics industry. The main problems that counterfeited chips cause are:
- Issues involving performance and reliability: Fake chips cannot work as well or last as long as genuine chips. They might be constructed from inferior materials or have not gone through the same rigorous quality and testing controls as real chips. This can result in a range of problems, from lower performance and longevity to total failure. In conclusion, this may result in malfunctions and unforeseen problems.
- Compatibility issues: Compatibility concerns may result in interoperability issues. This is because fake chips might not function well with other equipment or systems that they are intended to.
- Security risks: False chips can be used to break into secure systems and steal important information. For instance, fake chips might be used to create credit card scanners that steal customer payment information or gain access to crucial infrastructure systems, or they could be used to put people in danger. For instance, fake chips in medical equipment could make them malfunction and put people in danger.
- Economic and marketing harm: Counterfeit chips may cause financial loss to genuine producers and distributors as well as to final customers who unintentionally buy fraudulent products. The market for genuine products may be reduced by fake chips, making it more challenging for actual businesses to compete. Moreover, they undermine the reliability of electrical products. Customers lose trust in a brand and are less inclined to purchase its items in the future after learning that a product has counterfeit components.
- Legal and regulatory risks: The creation and sale of fake chips are prohibited in the majority of nations and may result in criminal charges, fines, and other sanctions. Companies that unknowingly buy fake chips risk legal and regulatory repercussions as well as reputational damage.
In general, counterfeit chips can provide major threats to people, businesses, and society. Thus, it is critical to take precautions to prevent and identify them wherever possible.
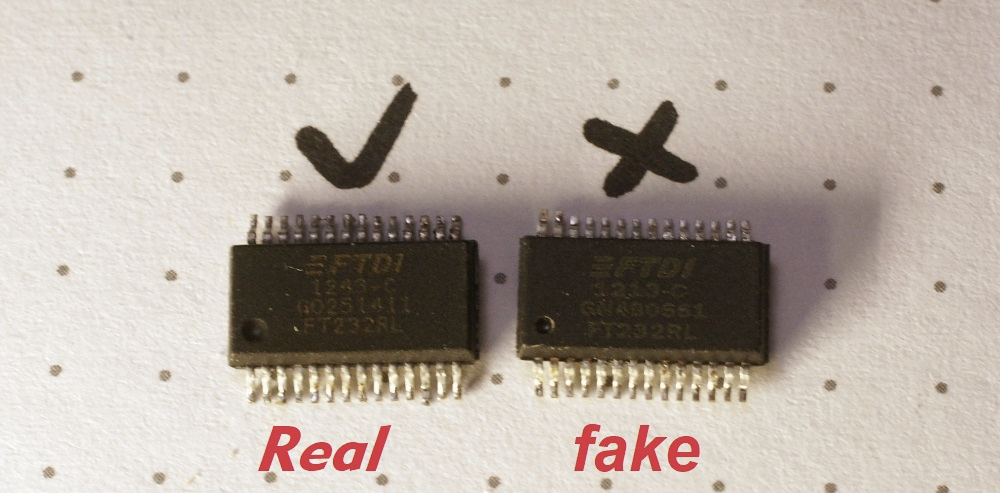
Figure 3: the difference between the fake and real chip in fonts and shapes
How to Prevent Buying a Counterfeited Chip?
When looking to purchase an ASIC chip, it is important to do your research to avoid purchasing a counterfeit. There are a few things you can do to help prevent buying a counterfeit ASIC:
There are several steps you can take to help prevent buying a counterfeit chip:
- Buy from reliable sources: Purchasing chips from reputable sources, such as authorized distributors or manufacturers, is one of the most critical procedures. These sources are more likely to have adequate quality control mechanisms in place to ensure the authenticity of the chips. Before making a purchase, read the seller’s internet reviews.
- Look for genuine markings: Most genuine chips have logos, serial numbers, or other identifying information. Verify to ensure that the markings are genuine and correspond to the requirements of the chip you are purchasing.
- Visual inspection: Examine the chip carefully for any evidence of tamperings, such as scratches or odd markings. Be on the lookout for common indications of counterfeit chips, such as misspellings or inaccurate logos.
- Inspect the packing: Be sure the packaging matches the original packaging for the chip you are buying. Examine for evidence of tampering or resealing.
- Employ advanced verification techniques: To ensure chip dependability, advanced verification techniques such as X-ray analysis and electrical testing can be applied. These approaches are more expensive and time-consuming than visual inspection, but they can provide great confidence in chip dependability.
- Be Wary of shadowy Low Prices: Fake chips are frequently sold at considerably lower prices than genuine chips, so be skeptical of deals that appear too good to be true.
By taking these precautions, you may limit your chances of obtaining counterfeit chips and receive real, trustworthy, and safe products.
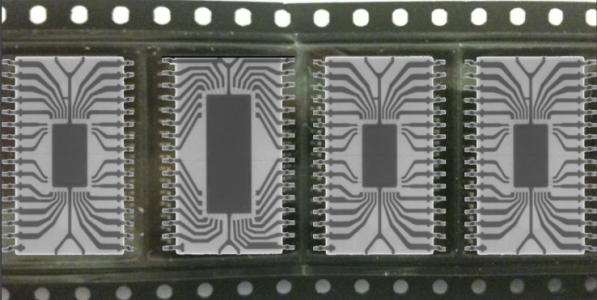
Figure 4: X-ray examining
Get in contact with Failure Analysis labs.
Conclusion
IC counterfeiting is becoming an increasingly common problem for companies using ASICs. Consumers should be aware of the hazards of buying chips and processors, given the advancement of technology and new ways to purchase counterfeit components. You can lessen your chance of encountering counterfeiters by taking the required precautions to ensure that you buy real goods. Reports from industry regulators should also aid in spotting questionable counterfeiting activity. Maintaining your company’s safety and security requires you to take steps to protect yourself from these hazards.
Next Steps
You can eliminate counterfeiting by manufacturing your own custom chip (ASIC). Click here to contact vendors.
![]()
![]()
![]()
![]()
![]()